Overview
ePass Montana will be decomissioned on June 30, 2022.
What level of effort can agencies expect for implementing Okta?
As you work to implement Login.mt.gov (Okta), it is important that the developers are familiar with SAML authentication. If your application is using a SAML solution (either a COTS product or ePass Montana), you should expect to spend approximately fifteen (15) hours of development work to implement Okta in an application. Agencies should follow standard regression testing for verifying internal and external authentication after the implementation work has been completed.
ePass Montana to Okta Migration Best Practices
This guide is intended for individuals responsible for maintaining or configuring Service Provider applications to aid in migrating from ePass Montana to Okta in a way that preserves as much user access and history as possible. Every Service Provider application is different and for that reason this guide focuses on strategy and Okta-specific configuration examples. If it is not necessary to maintain any information from ePass Montana and users can just use their new Okta accounts, it is not necessary to use the strategies in this document.
Developers
A good starting place is https://developer.okta.com. There you can find Okta's documentation as well as sign up for a free developer account that will give you a sandbox for experimenting with the Okta platform.
Another great source of information can be found on the IT Pro Page: IT Pro Page - Okta Information
The two primary authentication protocols available for your applications are OpenID Connect (OAuth) and SAML. For new application development, we recommend using OpenID Connect. You can find the well-known endpoints for the Okta OpenID Connect/OAuth authorization server at https://developer.okta.com/docs/reference/api/oidc/
We will have a ServiceNow form that the agency will fill out for an application registration into the Okta environments. We intend for SITSD to do the initial app registration and then delegate the "Application Administrator" role to the agency for any additional configuration changes and maintenance.
Public users will have an Okta account. They will login to this account using either Okta credentials (UserID and password) or a third-party social identity provider (e.g. Facebook, Google, Microsoft). State employees and contractors will use their Active Directory credentials to login to the Okta environment and applications.
Interface Requirements
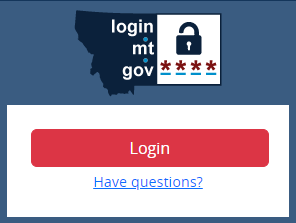
The below code snippets rely on Bootstrap 5:
HTML
<div id="okta-login" class="login-wrapper p-2">
<img class="logo d-block mx-auto mb-2" src="login-logo.png">
<div class="login-container bg-white text-center rounded p-4 d-grid gap-2">
<button type="button" class="btn btn-danger">Login</button>
<p class="m-0"><a href="https://okta.mt.gov/Help">Have questions?</a></p>
</div>
</div>
CSS
#okta-login a {
color: #0d6efd;
text-decoration: underline;
}
#okta-login a:hover {
color: #0a58ca;
text-decoration-thickness: 2px;
}
#okta-login.login-wrapper {
width: 300px;
margin: 30px auto;
text-align: center;
}
#okta-login .logo {
width: 150px;
}
#okta-login {
background-color: #3A5C81;
border: solid 1px #14365B;
}
#okta-login .btn-danger {
background: #dc3545;
border-color: #dc3545;
min-width: 26ch;
}
#okta-login .btn-danger:hover {
color: #fff;
background: #bb2d3b;
border-color: #b02a37;
}
Vertical Centering
When using Bootstrap 5, one of the ways this can be achieved by adding the below CSS to the body tag.
html, body {
height: 100%;
}
body {
display: -ms-flexbox;
display: flex;
-ms-flex-align: center;
align-items: center;
padding: 30px 0;
}
Alternate Display
Another display option would be to put the logo on a button that matches your application colors, like the below examples:
<button class="btn btn-danger fw-bold" type="button">
<img src="img/login-logo.png" class="d-block mx-auto">
Login
</button>